If malware is installed and then run on your computer, your computer is said to have a(n):
A) security hole B) infection C) hive D) cookie
B
You might also like to view...
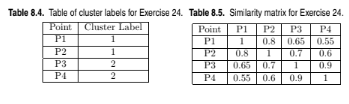
Given the set of cluster labels and similarity matrix shown in Tables 8.4 and 8.5, respectively, compute the correlation between the similarity matrix and the ideal similarity matrix, i.e., the matrix whose ijth entry is 1 if two objects belong to the same cluster, and 0 otherwise.
An app that performs synchronous tasks on a single-core computer often takes longer to execute than on a multi-core computer, because ________.
a) it’s too costly to convert them to asynchronous tasks b) the processor is shared between the app and all the others that happen to be executing on the computer at the same time c) multi-core computers have no overhead d) single-core compters generally have slower processors