If the acceptance strategy is used to handle every vulnerability in the organization, its managers may be unable to conduct proactive security activities and may portray an apathetic approach to security in general.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
A control is any graphical object on a form or a report that is used to display data, perform an action, or make a form or report easier to read
Indicate whether the statement is true or false
Computer Science & Information Technology
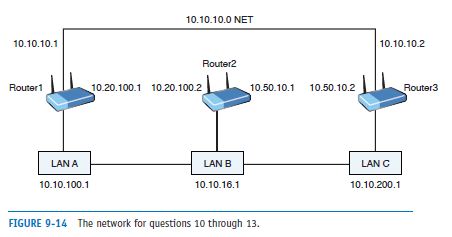
List two static routes to route data from LAN A to LAN C in the network shown in Figure 9-14, assuming the subnet mask 255.255.255.0.
Computer Science & Information Technology