List two static routes to route data from LAN A to LAN C in the network shown in Figure 9-14, assuming the subnet mask 255.255.255.0.
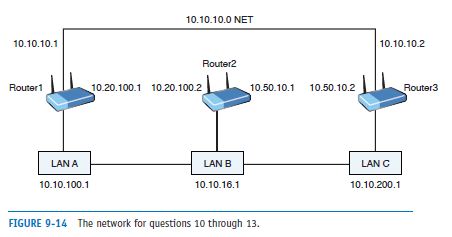
ip route 10.10.200.0 255.255.255.0 10.10.10.2
ip route 10.10.200.0 255.255.255.0 10.20.100.2
Computer Science & Information Technology
You might also like to view...
One of the most basic methods attacker could use to identify active machines is to perform a ping sweep
Indicate whether the statement is true or false.
Computer Science & Information Technology
One problem with posttest loops is that they always execute at least once. You can fix the problem in the Posttest Loop button's code by placing the posttest loop in a(n) ____ structure.
A. selection B. execute C. iterative D. another posttest loop
Computer Science & Information Technology