What is the next hop address for the FastEthernet port 2 on Router C in Figure 8-12?
Figure 8-12
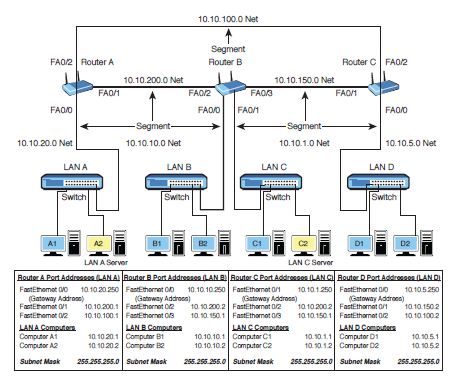
Router A, FA0/2, 10.10.100.1
Computer Science & Information Technology
You might also like to view...
When an application is secure without having to change any default settings it is said to be what?
A. secure by design B. secure by default C secure by deployment D. secure by reference
Computer Science & Information Technology
Sue was required to sign an NDA when she took a job at her new company. Why did the company require her to sign it?
A. To protect the confidentiality of their data B. To ensure that Sue did not delete their data C. To prevent Sue from directly competing with them in the future D. To require Sue to ensure the availability for their data as part of her job
Computer Science & Information Technology