If a technician was going to test connectivity on port 25, which of the following application type is being checked?
A. FTP
B. DNS
C. Mail
D. Telnet
Ans: C. Mail
Computer Science & Information Technology
You might also like to view...
Security should be enabled on workbooks containing macros because they can be used to spread ________
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
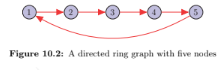
Consider a five-node directed ring graph, as shown in Figure 10.2. Identify a matrix op- erator using (a) the weight matrix, (b) the in-degree directed Laplacian, and (c) the out- degree directed Laplacian of the graph that shifts a signal one step left. That is, for a signal [1 , 2 , 3 , 4 , 5] T , the shifted version should be [2 , 3 , 4 , 5 , 1] T
Computer Science & Information Technology