List all the possible routes from LAN B to LAN D in the network shown in Figure 8-12.
Figure 8-12
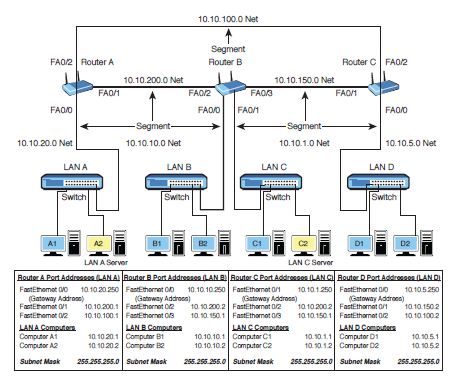
LAN B > Router B > Router C > LAN D (2 hops)
LAN B > Router B > Router A > Router C > LAN D (3 hops)
Computer Science & Information Technology
You might also like to view...
Most instance variables are declared ________.
a) public b) protected c) private d) None of the above.
Computer Science & Information Technology
You can use five anti-aliasing methods: None, Sharp, ____________________, Strong, and Smooth.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology