Match the decription on the right to the section of the URL identified in the following diagram.
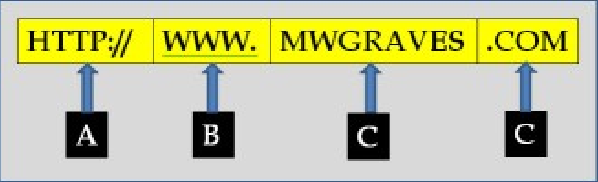
1. Schema
2. Server location
3. User domain
4. Top level domain
a. A
b. D
c. B
d. C
A 1. Schema
C 2. Server location
D 3. User domain
B 4. Top level domain
Computer Science & Information Technology
You might also like to view...
If user accounts are set up, the user may be required to ________ the user icon to log in
A) clip B) click C) snap D) press
Computer Science & Information Technology
If there were frequent physical security breaches, what would documentation at the work instruction level include?
What will be an ideal response?
Computer Science & Information Technology