An aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him- or herself is known as ________
Fill in the blank(s) with the appropriate word(s).
Answer: cyberbullying
Computer Science & Information Technology
You might also like to view...
A user reports that they are unable to connect to the network. Upon further investigation, a technician notices that the user has an IP address/subnet mask combination of 192.168.204.255/24. The default gateway for the network is 192.168.204.254. Which of the following could the user's IP address be changed to so that they could connect to the network?
A. 192.168.204.0/27 B. 192.168.204.1/27 C. 192.168.204.112/24 D. 192.168.204.254/24
Computer Science & Information Technology
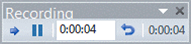
A. slide B. sound byte C. animation D. content placeholder
Computer Science & Information Technology