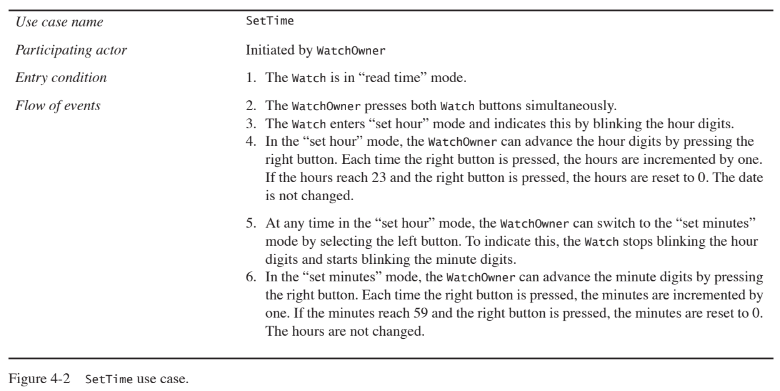
Consider the scenario you wrote in Exercise 4-1 Identify the actor of the scenario. Next, write the corresponding use case SetTime. Include all cases, and include setting the time forward, backward, setting hours, minutes, and seconds.
What will be an ideal response?
The following use case is generalized from the scenario of Figure 4-1. The level of detail of the use case should be the
same as the level of detail of the scenario in the previous exercise.

Computer Science & Information Technology
You might also like to view...
To ________ a table means to arrange the data in a specific order
Fill in the blank(s) with correct word
Computer Science & Information Technology
S/MIME provides authentication through the use of _________ .
A. asymmetric block encryption B. symmetric block encryption C. radix-64 D. digital signatures
Computer Science & Information Technology