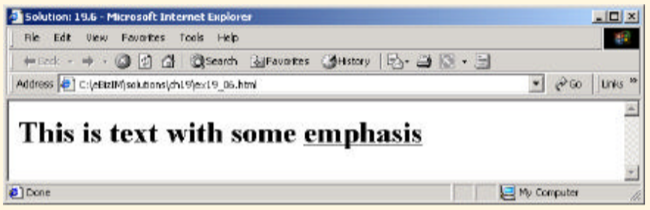
Create a CSS rule that changes the effect of an EM element from italic text to underlined text.
What will be an ideal response?
```
1
2
3
4
5
6
7
8
12
13
14
15
This is text with some emphasis
16
17
```
Computer Science & Information Technology
You might also like to view...
The keyword used in SQL to establish specify the table where the fields can be found is ________
Fill in the blank(s) with correct word
Computer Science & Information Technology
An attacker to a network is using social engineering to attack a network. This means which of the following? (Select all that apply.)
A) The attacker uses a dictionary attack. B) The attacker uses packet sniffing. C) The attacker claims to be from network support. D) The attacker is sifting through discarded trash.
Computer Science & Information Technology