Which of the following is not true of system penetration?
a) Every system penetration is potentially dangerous.
b) It is a successful breach of a system’s security.
c) It leads to denial of service.
d) Many attacks rely on a successful system penetration.
c) It leads to denial of service.
Computer Science & Information Technology
You might also like to view...
A network technician needs to configure a port on a switch to provide connectivity and electrical support to a WAP being installed in a warehouse. Which of the following features needs to be configured on the switch?
A. STP B. PoE C. VTP trunking D. Port forwarding
Computer Science & Information Technology
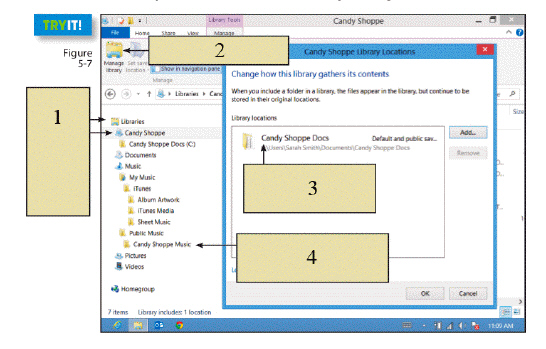 In the figure above, item 1 shows you where to create a(n) ____.
In the figure above, item 1 shows you where to create a(n) ____.
A. custom library B. Manage library icon C. library folder D. "real" location
Computer Science & Information Technology