In the Needham and Shroeder authentication protocol with secret keys, explain why the following version of message 5 is not secure:
![]()
The purpose of message 5 is for A to convince B that 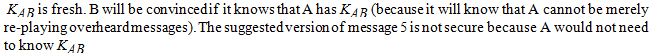 in order to send it, it could be sent by copying message 4.
in order to send it, it could be sent by copying message 4.
Computer Science & Information Technology
You might also like to view...
Case based critical thinking ? Case 13-3 ? Thomas is working on reference forms and form fields. He wants to use event handlers that can respond to user actions within a form. He uses theelement.onchangeevent handler. Identify the description of the event handler Thomas has used.
A. Theelementhas received user input B. The value ofelementhas been modified C. Theelementvalue is invalid D. The formelementhas lost the focus
Computer Science & Information Technology
What is a Gantt chart?
What will be an ideal response?
Computer Science & Information Technology