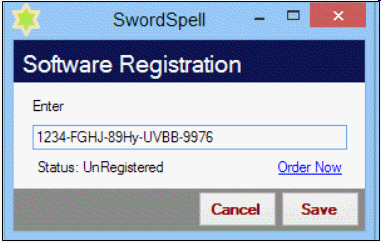
 If the key to be entered into the text box in the accompanying figure is long, you should _____________.
If the key to be entered into the text box in the accompanying figure is long, you should _____________.
A. type it carefully
B. copy and paste it into the provided box
C. request an encrypted short key
D. none of the above
Answer: B
Computer Science & Information Technology
You might also like to view...
A __________ attack occurs when an attacker continually bombards a wireless access point or some other accessible wireless port with various protocol messages designed to consume system resources.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The Application Guide is the key to software reusability.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology