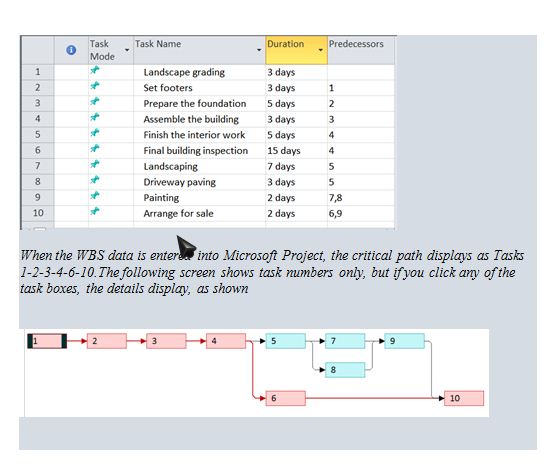
What is the critical path?
What will be an ideal response?
Assume that students have numbered the tasks as shown in the following WBS:
Computer Science & Information Technology
You might also like to view...
What is the Nmap utility used for?
a. It is used to identify unsecured sensitive data on the network, such as credit cards. b. It is an automated vulnerability and penetration testing framework. c. It is a software firewall that can be used to secure a vulnerable host. d. It is a port scanning utility that can identify open ports on a host.
Computer Science & Information Technology
The Color list arrow appears in the New ____________________ dialog box.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology