Update the class diagrams of Figure 5-29 and Figure 5-31 to include the new objects you identified in Exercise 5-11.
What will be an ideal response?
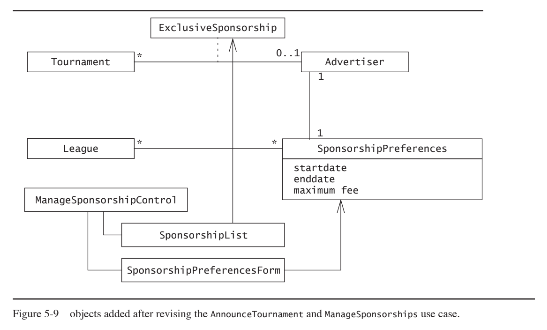
Figure 5-9 depicts the objects discussed in Exercise 5-11 and their associations.
Computer Science & Information Technology
You might also like to view...
Mail servers may block e-mails with attached file types with ________ enabled
A) saving B) file names C) contents D) macros
Computer Science & Information Technology
TLS requires both the client and the server use these to verify their identities.
What will be an ideal response?
Computer Science & Information Technology