The ethical hacking report contains highly sensitive information and should be protected at all times
Indicate whether the statement is true or false.
ANS: True
Computer Science & Information Technology
You might also like to view...
Word numbers captions sequentially as they are added to the document
Indicate whether the statement is true or false
Computer Science & Information Technology
FIGURE AC 5-1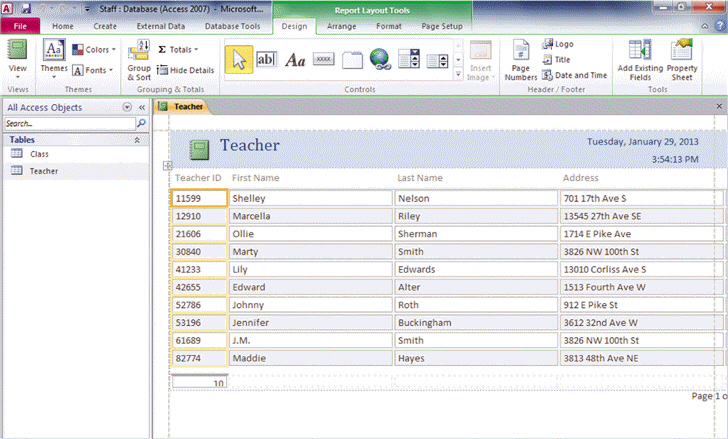 Referring to the figure above, in this report, ____ appear in controls.
Referring to the figure above, in this report, ____ appear in controls.
A. the Teacher ID label B. the records shown below the Teacher ID label C. both a. and b. D. neither a. nor b.
Computer Science & Information Technology