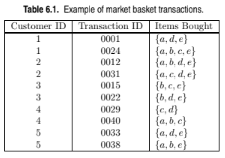
Compute the support for itemsets {e}, {b, d}, and {b, d, e} by treating each transaction ID as a market basket.
Consider the data set shown in Table 6.1.
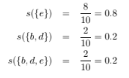
Computer Science & Information Technology
You might also like to view...
There are ________ alignment options to position text in a cell
A) three B) four C) six D) nine
Computer Science & Information Technology
You have been tasked with implementing a VPN server that will allow clients to connect from mobile networks and from networks that utilize restrictive firewalls. What VPN tunneling protocol has be best chance to be successful, given the constraints?
A. Point-to-Point Protocol B. Point-to-Point Tunneling Protocol C. Layer Two Tunneling Protocol D. Secure Socket Tunneling Protocol
Computer Science & Information Technology