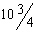 The buttons marked 5 in the accompanying figure are the ____ buttons.
The buttons marked 5 in the accompanying figure are the ____ buttons.
A. standard
B. folder
C. function
D. start
Answer: A
You might also like to view...
In a salami-slicing attack, a program performs a large number of small, hardly noticeable malicious actions, which add up to a large aggregate malicious action. In a classic example, a programmer for a bank has 1 cent of the monthly interest calculation on each bank customer's account transfered into his account. Thus, if the bank has 1,000,000 customers, then this programmer would get $10,000
each month from this salami slicing attack. What type of malware is such a program? What will be an ideal response?
Develop a process for managing change requests and design a form to handle a generic change request. The process should include a contingency plan for changes that must be resolved immediately.
What will be an ideal response?