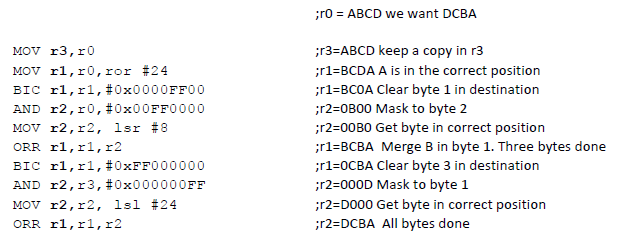
A memory mapped input device in an ARM environment returns a 32?bit four?byte value in the order ABCD. The processor needs the byte in the order DCBA. Write a fragment of ARM code to perform the transformation.
What will be an ideal response?
Using the source word ABCD with the order byte 3, byte 2, byte 1, byte 0.
You might also like to view...
An employee of your company files a complaint with a security administrator. While sniffing network traffic, the employee discovers that financially confidential emails were passing between two warehouse users. The two users deny sending confidential emails to each other. You need to allow for non-repudiation and prevent network sniffers from reading the confidential mail. What should you do?
A. Implement transport encryption and authentication hashing. B. Implement transport encryption and legal mail hold. C. Implement legal mail hold and authentication hashing. D. Implement transport encryption and digital signatures.
Which of the following is false?
a. You should not call overridable methods from constructors—when creating a subclass object, this could lead to an overridden method being called before the subclass object is fully initialized. b. It’s OK to any of a class’s methods from its constructors. c. When you construct a subclass object, its constructor first calls one of the direct superclass’s constructors. If the superclass constructor calls an overridable method, the subclass’s version of that method will be called by the superclass constructor. d. It’s acceptable to call a static method from a constructor.