The principal object of a hash function is __________ .
A. data integrity
B. compression
C. collision resistance
D. mapping messages
A. data integrity
Computer Science & Information Technology
You might also like to view...
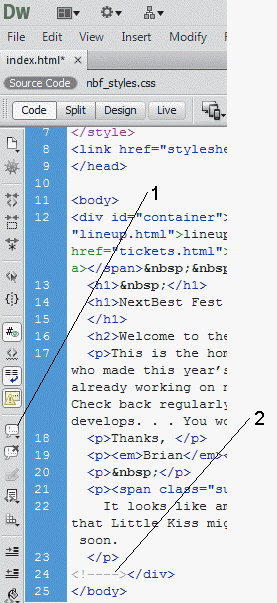 The item marked 2 in the accompanying figure shows the ____________________ code added before the closing div tag.
The item marked 2 in the accompanying figure shows the ____________________ code added before the closing div tag.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What makes ____________________ (that is, sociopathic behavior specific to the Internet) particularly troubling is that the Internet seems to be making these behaviors easier.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology