Lisa, a technician, is troubleshooting a laptop's connection to a wireless network and notices the user has placed their cell phone on top of the wireless router. Which of the following is the cell phone MOST likely generating?
A. Wrong encryption
B. An SSID mismatch
C. Latency
D. Interference
Answer: D. Interference
Computer Science & Information Technology
You might also like to view...
The control variable of a counter-controlled loop should be declared as ________to prevent errors.
a. int. b. float. c. double. d. Any of the above.
Computer Science & Information Technology
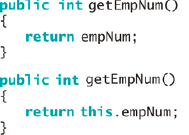
What will be an ideal response?
Computer Science & Information Technology