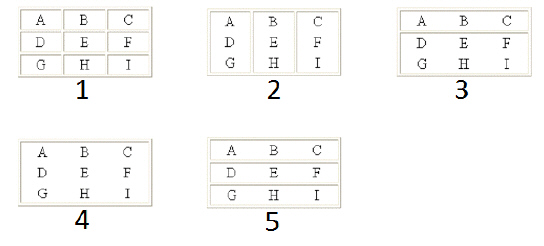
 The table marked 2 in the accompanying figure has a rules value of ____.
The table marked 2 in the accompanying figure has a rules value of ____.
A. all
B. cols
C. rows
D. void
Answer: B
Computer Science & Information Technology
You might also like to view...
Which cyber defense concept suggests limiting permissions to only what is necessary to perform a particular task?
A. Authentication B. Authorization C. Defense in depth D. Principle of least privilege
Computer Science & Information Technology
Which command can be run on a workstation to determine the Group Policies applied on a workstation?
a. extract b. tasklist c. gpupdate d. gpresult e. chkdsk
Computer Science & Information Technology