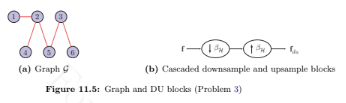
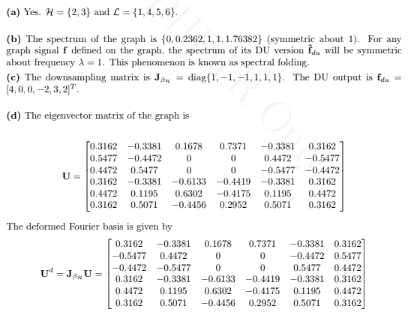
Consider the graph shown in Figure 11.5(a).


Computer Science & Information Technology
You might also like to view...
Which of the following statements best describes a Trojan?
A) Malicious software that hides into the lower levels of the operating system and opens a backdoor B) Malicious software that records every key stroke and mouse movement C) Malicious software that disguises itself as a legitimate program D) Malicious software that takes the computer data hostage to extort money
Computer Science & Information Technology
____ is a language that can be used in Visual Studio.
A. Fortran B. Visual F# C. Lisp D. COBOL
Computer Science & Information Technology