The purpose of the __________ algorithm is to enable two users to securely reach agreement about a shared secret that can be used as a secret key for subsequent symmetric encryption of messages.
Fill in the blank(s) with the appropriate word(s).
Diffie-Hellman Key Agreement
Computer Science & Information Technology
You might also like to view...
Narrator is an example of a screen reader program
Indicate whether the statement is true or false
Computer Science & Information Technology
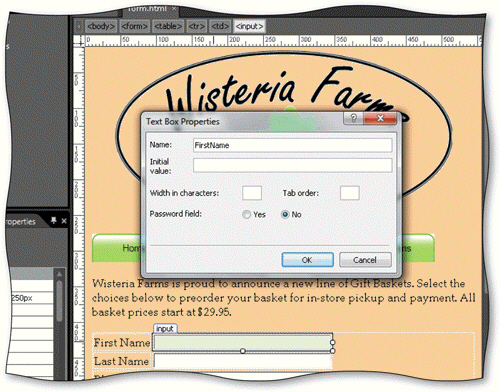 Using the accompanying figure as your guide, briefly list the steps to assign properties to a text box control.
Using the accompanying figure as your guide, briefly list the steps to assign properties to a text box control.
What will be an ideal response?
Computer Science & Information Technology