Which of the following Trojans enables the hacker to turn on the webcam and record audio?
a. Sub Seven
b. Poison ivy
c. GhostRat
d. Tini
ANS: C
Computer Science & Information Technology
You might also like to view...
At a rented house that does not have Internet access, two people need to share files. Neither has a flash drive. What type of network would help in this situation?
A) Bluetooth B) Ad hoc C) WiMAX D) USB
Computer Science & Information Technology
FIGURE EX 4-1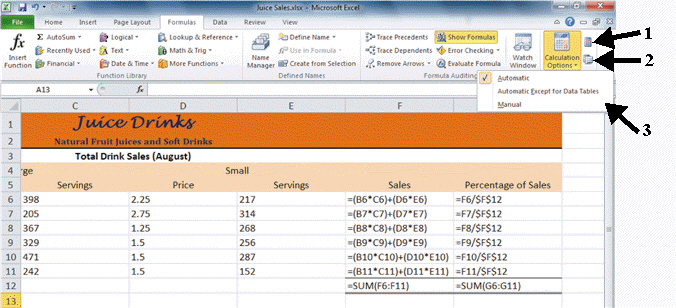 In Figure EX 4-1 above, number 1 is pointing to the ____ button.
In Figure EX 4-1 above, number 1 is pointing to the ____ button.
A. Show Now B. Calculate Formulas C. Calculate Now D. Calculate Sheet
Computer Science & Information Technology