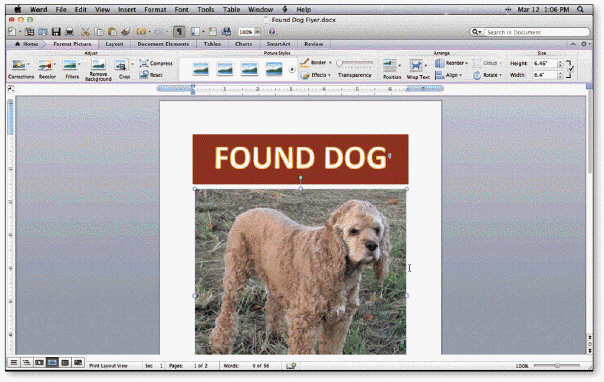
 The small squares and circles around a selected graphic, as shown in the accompanying figure, are called ____ handles.
The small squares and circles around a selected graphic, as shown in the accompanying figure, are called ____ handles.
A. sizing
B. shape
C. base
D. dimension
Answer: A
Computer Science & Information Technology
You might also like to view...
What communications technique can a hacker use to identity the product that is running on an open port facing the Internet?
a. Credentialed penetration test b. Banner grabbing c. Intrusive vulnerability scan d. Port scanning
Computer Science & Information Technology
Create a bird's-eye view of an interface you wish to investigate. Focus on detecting inconsistencies and spotting unusual patterns.
What will be an ideal response?
Computer Science & Information Technology