Bob sends Alice an encrypted message using AES. What key would Alice need to use to decrypt the message?
A. Bob's public key
B. Bob's private key
C. Alice's public key
D. The same key that Bob used to encrypt the message
Answer: D
Explanation: AES is a private/symmetric key algorithm. Symmetric key encryption uses one shared key to encrypt and decrypt data, so Alice needs to use the same key Bob used to encrypt the data to decrypt the message.
You might also like to view...
(Drawing Patterns with Nested for Loops) Write a program that uses for statements to print the following patterns separately, one below the other. Use for loops to generate the patterns. All asterisks (*) should be printed by a single statement of the form cout << '*'; (this causes the asterisks to print side by side). [Hint: The last two patterns require that each line begin with an ap- propriate number of blanks. Extra credit: Combine your code from the four separate problems into a single program that prints all four patterns side by side by making clever use of nested for loops.]
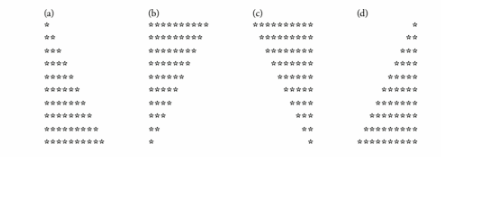
What will be an ideal response?
Programming languages that use symbolic notation like ADD 1, 2 are referred to as ____.
a. assembly languages b. machine languages c. opcode languages d. IBM languages