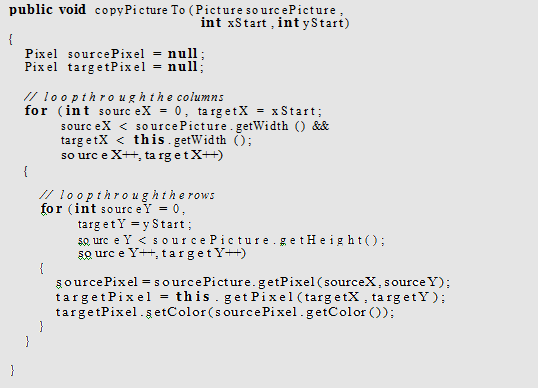
Modify the general copy method copyPictureTo in Chapter 5 to stop looping if it is past the width of either the source picture or the current picture.
What will be an ideal response?
Computer Science & Information Technology
You might also like to view...
Which IPv6 multicast addresses are used by OSPFv3 for communications between OSPFv3-configured devices?
A) FF02::5 B) FF02::6 C) FF02::A D) FF02::9
Computer Science & Information Technology
A(n) ____ attack occurs when an attacker disrupts normal computer processing or denies processing entirely.
A. ?necessity B. ?integrity C. ?secrecy D. ?man-in-the-middle
Computer Science & Information Technology