This is when the attacker uses every possible combination of characters for the password.
What will be an ideal response?
brute force
Computer Science & Information Technology
You might also like to view...
Use the ________ function to combine text from multiple columns
Fill in the blank(s) with correct word
Computer Science & Information Technology
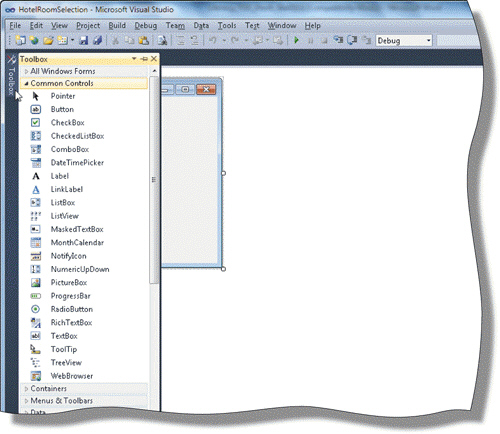 When the Pushpin icon on the Auto Hide button is vertical, the part of the Visual Studio window shown in the accompanying figure is said to be in ____________________ mode.
When the Pushpin icon on the Auto Hide button is vertical, the part of the Visual Studio window shown in the accompanying figure is said to be in ____________________ mode.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology