Outsiders might try to infect your system through all of the following, EXCEPT ________
A) contaminated USB drives
B) e-mail messages
C) Bluetooth pairing
D) Internet downloads
C
Computer Science & Information Technology
You might also like to view...
After the conclusion of any criminal trial, if it becomes evident that an appeal is not possible, all contraband must be destroyed
a. True b. False
Computer Science & Information Technology
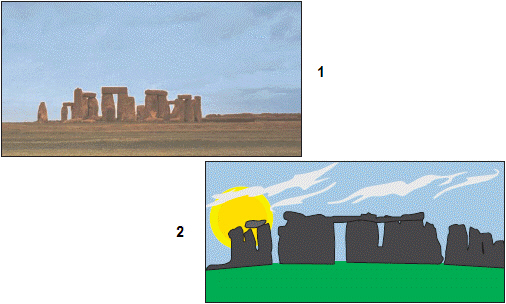 In the figure above, image 2 is a ____.
In the figure above, image 2 is a ____.
A. bitmap graphic B. scanned image C. vector graphic D. digitized image
Computer Science & Information Technology