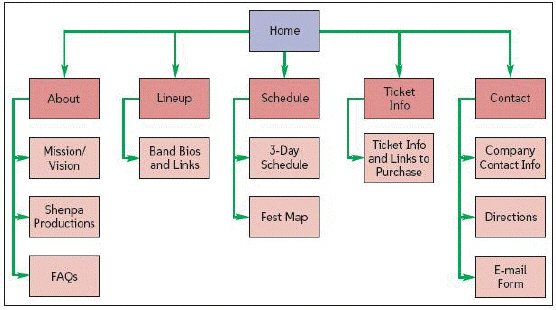
 In an item like the one in the accompanying figure, the lines represent steps, decision points, and dead ends.
In an item like the one in the accompanying figure, the lines represent steps, decision points, and dead ends.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
The Validation Rule Like "[A-Z*@[A-Z].gov" specifies that a Web site must be a(n) ________ one
Fill in the blank(s) with correct word
Computer Science & Information Technology
Which of the following are examples of penetration testing methods? (Select the two best answers.)
A. The open source security testing methodology manual B. OVAL C. NIST penetration testing D. CERDEC
Computer Science & Information Technology