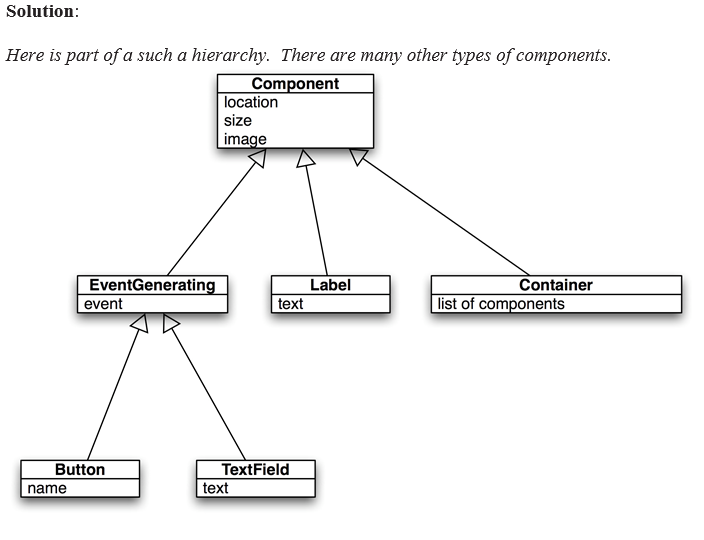
Draw a hierarchy for the components you might find in a graphical user interface. Note that some components can trigger actions. Some components may have graphics associated with them. Some components can hold other components.
What will be an ideal response?
Computer Science & Information Technology
You might also like to view...
A ________ occurs when an action is completed on any given object. The action could be, for example, a simple click of the mouse or entering information into a specific field
A) modal message B) submacro C) database event D) command
Computer Science & Information Technology
Which of the following is true about symmetric encryption?
A. It uses a secret key to encrypt and decrypt. B. It uses a private and public key. C. It is also known as public key encryption. D. It requires four keys to hold a conversation.
Computer Science & Information Technology