Pam's boss, Alan, says that she needs to write her software so that it is protected against the security risks of today and tomorrow. How is this even possible, given that we don't even know what the security risks of tomorrow are?
What will be an ideal response?
Alan is probably trying to get Pam to use good software practices, such as code
walkthroughs, software visualization, team programming, and avoid buffer overflows. These
practices can reduce software vulnerabilities that could be exploited in the future.
Computer Science & Information Technology
You might also like to view...
A(n) ____________________ indicates a variable has no value assigned to it.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
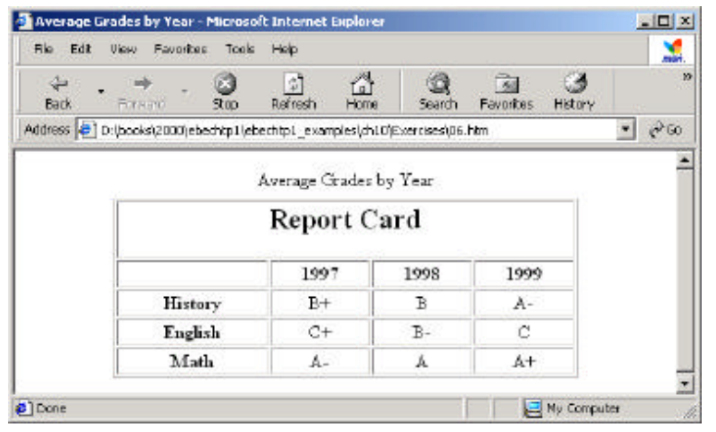
Write the HTML code that produces the following Web page. The width of the table is 400 pixels and the border is one pixel wide. The header is enclosed in an H2 element.
Computer Science & Information Technology