The ____ exploit is more characteristic of an attacker who has insider knowledge, or who might be an actual insider.
A. zero-knowledge
B. partial-knowledge
C. closed-knowledge
D. full-knowledge
Answer: D
Computer Science & Information Technology
You might also like to view...
Which of the following is TRUE about reusing slides from an existing presentation in PowerPoint 2013?
A) To start the process, click the File tab. B) When you insert a slide into an open presentation, the slide takes on the formatting of the current presentation. C) Slides can only be reused from versions older than PowerPoint 2013. D) The file from which you are reusing slides must be open.
Computer Science & Information Technology
Name the organizational scheme used in each of the following examples. Justify your answer.
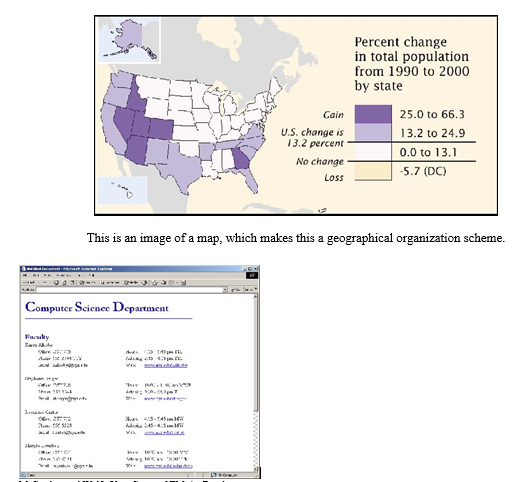
This is an image of a map, which makes this a geographical organization scheme.
Computer Science & Information Technology