The ability of any computer to imitate another computer is known as
a. mimicry
b. the Imitation Principle
c. the Universality Principle
d. the Turing test
c. the Universality Principle
Computer Science & Information Technology
You might also like to view...
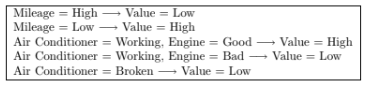
Are the rules mutually exclustive?
Consider a binary classification problem with the following set of attributes
and attribute values:
• Air Conditioner = {Working, Broken}
• Engine = {Good, Bad}
• Mileage = {High, Medium, Low}
• Rust = {Yes, No}
Suppose a rule-based classifier produces the following rule set:
Computer Science & Information Technology
____________________ are compromised systems that are directed remotely (usually by a transmitted command) by the attacker to participate in an attack.
A. Drones B. Helpers C. Zombies D. Servants
Computer Science & Information Technology