____ is implemented by a formal, organization-wide physical security plan.
A. Logical security protection
B. Virtual security protection
C. Physical security protection
D. Tangible security protection
Answer: C
Computer Science & Information Technology
You might also like to view...
When an object of a subclass is instantiated, a superclass _____________ is called implicitly or explicitly.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
FIGURE AC 3-1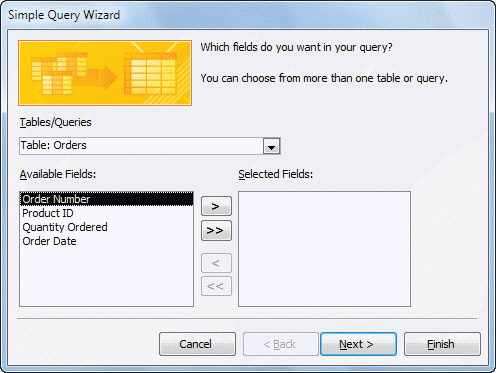 You use the Tables/Queries arrow in the dialog box shown in Figure AC 3-1 above to select the ____ that contains the data you want your new query to display.
You use the Tables/Queries arrow in the dialog box shown in Figure AC 3-1 above to select the ____ that contains the data you want your new query to display.
A. table B. query C. either a. or b. D. neither a. nor b.
Computer Science & Information Technology