____________________ involves pretending-typically via phone or e-mail-to be a bank officer, potential employer, IT employee, or other trusted individual in order to get the potential victim to supply personal information.
Fill in the blank(s) with the appropriate word(s).
Social engineering
You might also like to view...
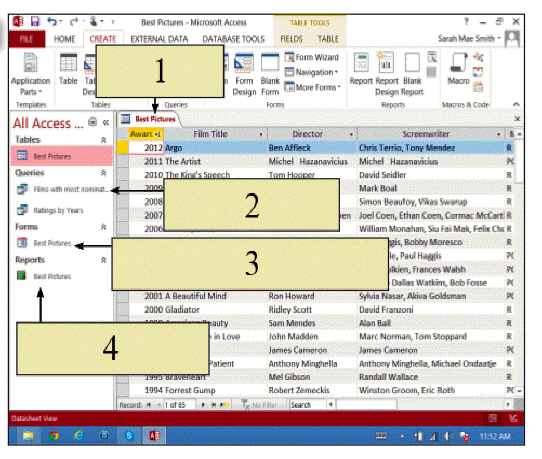 In the accompanying figure, item 4 ____.
In the accompanying figure, item 4 ____.
A. holds the records that contain data B. searches through the records C. defines a way of displaying the data in each record D. organizes and displays data in an effective way
You have decided that you will design a title so that it looks good in any screen resolution from 640x480 to 1024x768. You want the heading to be dramatic, which you have decided means as big as possible without it breaking into two lines on a small screen. The title is “Typography is Fun!” Create a Web page with several versions of the title, each using a different typeface. Use at least different three different typefaces. For each version, specify the typeface and size for the font. Note: there is no unique “correct” answer. Restrict yourself to the typefaces described in this chapter.
What will be an ideal response?