Some attackers want to be hidden from network devices or IDSs that recognize an inordinate amount of pings or packets being sent to their networks. Which of the following attacks are more difficult to detect?
A. stealth
B. silent
C. planned
D. covert
Answer: A
Computer Science & Information Technology
You might also like to view...
A ________ topology uses more than one topology when building a network
A) crossover B) multiple-use C) fusion D) hybrid
Computer Science & Information Technology
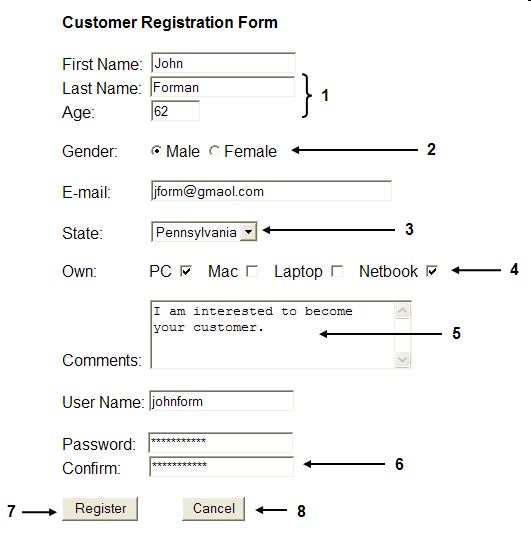 The default width for a text box, such as the one labeled "First Name" in the accompanying figure, is ____ characters.
The default width for a text box, such as the one labeled "First Name" in the accompanying figure, is ____ characters.
A. 10 B. 15 C. 20 D. 25
Computer Science & Information Technology