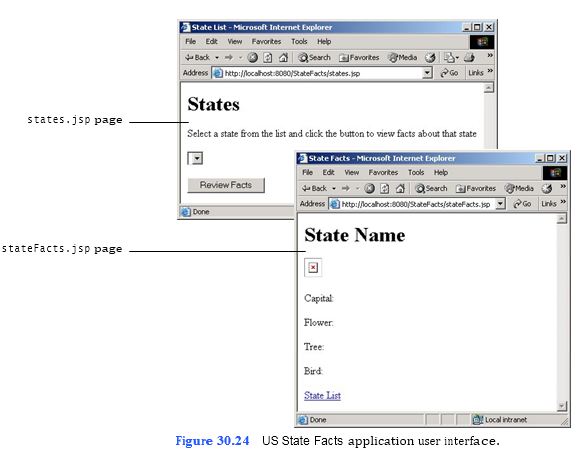
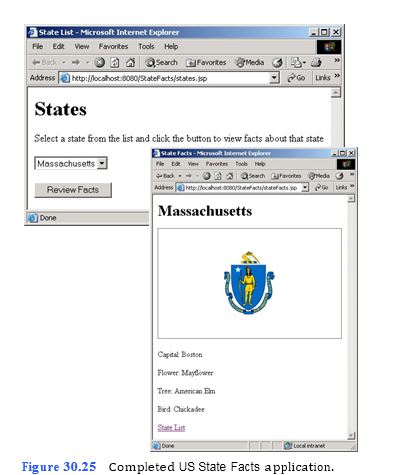
Create the user interface for the US State Facts application. The detailed description of this application can be found in Exercise 29.12. The design for the two pages for this application is displayed in Fig. 30.24. You will develop this application over this and the next two tutorials, so you do not yet have the state names, images and information from the database. To help you to better understand what you are setting out to do, Figure 30.25 shows a test-drive-like full final screen output.
a) Copying the template to your working directory. Copy the C:Examples Tutorial30ExercisesStateFacts directory to the C:SimplyJava directory.
b) Opening the states.jsp template file. Open the states.jsp file in your text editor. c) Setting the title of states.jsp. Add a title element to set the JSP’s title to “State
List.”
d) Adding an h1 header element to states.jsp. Add an h1 header element that dis- plays “States.”
e) Adding a form to states.jsp. Add an HTML form element.
f) Adding a paragraph to states.jsp. Within the form element, add a paragraph that displays the instruction “Select a state from the list and click the button to view facts about that state.”
g) Adding a menu control to states.jsp. Within the form element, add a select ele- ment. The name attribute for the
```
1
2
3
4
5
6
7
8
9
10
11
12
13
14
States
15
16
17
31
32
```
```
1
2
3
4
5
6
7
8
9
10
11
12
13
14
State Name
15
16
17
18
19
20
Capital:
21
22
23
Flower:
24
25
26
Tree:
27
28
29
Bird:
30
31
32
33
34
35
```
You might also like to view...
________ are not enabled by default and are quick short gestures in a diagonal direction that either delete, copy, paste, or undo
A) Editing flicks B) Navigational flicks C) Gesture flicks D) Custom flicks
The virus/worm that specifically targets Macintosh computers is ________
a. W32/Netsky-P b. Troj/Invo-Zip c. MacDefender d. None of the above