The ER diagram in Figure 17.13 shows only entities and primary key attributes. The absence of recognisable named entities or relationships is to emphasize the rule-based nature of the mapping rules described in Step 2.1 of logical database design.
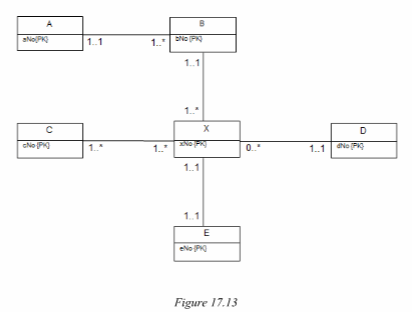
Answer the following questions with reference to how the ER model in Figure 17.13 maps to relational tables.
(a) How many relations will represent the ER model?
(b) How many foreign primary keys are mapped to the relation representing X?
(c) Which relation(s) will have no foreign key?
(d) Using only the letter identifier for each entity, provide appropriate names for the
relations mapped from the ER model.
(e) If the cardinality for each relationship is changed to one-to-one with total participation
for all entities; how many relations would be derived from this version of the ER model?
(a) How many relations will represent the ER model? 6
(b) How many foreign primary keys are mapped to the relation representing X?
2 - The primary keys of entities X and D as they have a 0ne-to-many relationship with X and
they are on the one side and therefore send a copy of their primary keys to X. Once mapped to
X – the copies of primary keys are referred to as foreign keys.
(c) Which relation(s) will have no foreign key?
Relations A, C and D
(d) Using only the letter identifier for each entity, provide appropriate names for the
relations mapped from the ER model.
Relation A
Relation B
Relation C
Relation CX (Representing the many-to-many relationship between entities C and X)
Relation XE (Entity X and E merge as there is a one-to-one relationship with total (i.e. full)
participation relating these entities).
Relation D
(e) If the cardinality for each relationship is changed to one-to-one with total participation
for all entities; how many relations would be derived from this version of the ER model?
1 (Relation ABCXDE)
You might also like to view...
A(n) __________________ is an application that displays the inner workings of an executing program.
a) stethoscope b) telescope c) debugger d) signal analyzer e) oscilloscope
You have set up a user group named Accounting and have put all employees in the Accounting department in this group, which has been given permission to use the Financial folder on a file server. You are now asked to create a subfolder under Financial named Payroll. Megan, the payroll officer, is the only employee in the Accounting department allowed to access this folder. What is the best way to configure the new share?
a. Assign Megan read/write permissions to the Payroll folder, and explain to your boss that it is not a best practice to give only one employee access to an important folder. b. Assign Megan read/write permissions to the Payroll folder. c. Create a new user group named Payroll, put Megan in the group, and assign the group read/write permissions to the Payroll folder. d. Ask your boss to allow you to put the folder outside of the Financial folder so you can assign a new user group read/write permissions to this folder that will not conflict with the Accounting user group.