__________ aggregates log and event data from virtual and real networks, applications, and systems. This information is then correlated and analyzed to provide real-time reporting and alerting on information/events that may require intervention or other type of response.
Fill in the blank(s) with the appropriate word(s).
Identity and access management (IAM)
Computer Science & Information Technology
You might also like to view...
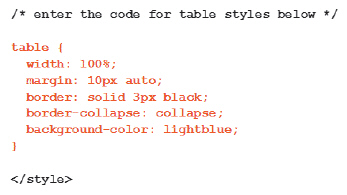 In the accompanying figure, the table width is 100% of the ____ section.
In the accompanying figure, the table width is 100% of the ____ section.
A. background B. border C. container D. body
Computer Science & Information Technology
What are the two levels of privileges which can be granted in Oracle?
What will be an ideal response?
Computer Science & Information Technology