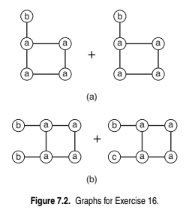
Draw all candidate subgraphs obtained from joining the pair of graphs shown in Figure 7.2. Assume the edge-growing method is used to expand the sub- graphs.
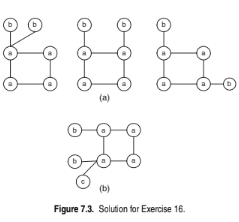
See Figure 7.3.
Computer Science & Information Technology
You might also like to view...
A user is unable to connect to a network with encryption. The user is able to see the network and has the correct passphrase. Which of the following is MOST likely the problem?
a) Encryption type b) SSID mismatch c) Standard mismatch d) Signal strength
Computer Science & Information Technology
How does the Inter-Access Point Protocol (IAPP) enable roaming communications?
What will be an ideal response?
Computer Science & Information Technology