Provide an implementation of pthread_barrier_init and pthread_barrier_destroy to go along with the implementation of pthread_barrier_wait from Exercise 11.5. Don’t bother supporting any barrier attributes for now.
What will be an ideal response?
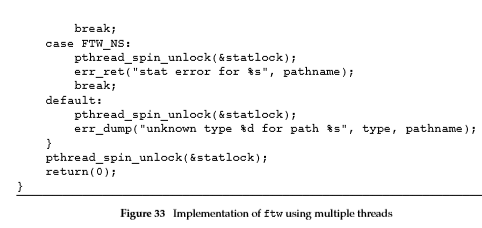
The solution is shown in Figure34.

Computer Science & Information Technology
You might also like to view...
What is an argument in a function? Give an example
What will be an ideal response?
Computer Science & Information Technology
Any attempt to manipulate information in pursuit of a military or political goal is ________
a. Cyberterrorism b. Economic terrorism c. Information warfare d. None of the above
Computer Science & Information Technology