The first step in any cybersecurity process is to ____.
A. get it properly organized
B. get as much information as possible
C. make the controls as strong as possible
D. move as fast as possible
Answer: A
Computer Science & Information Technology
You might also like to view...
Including what, distorts the effectiveness of charting data points?
A) Too many series B) Aggregates C) Too many data points D) Too much variance in the values of the data
Computer Science & Information Technology
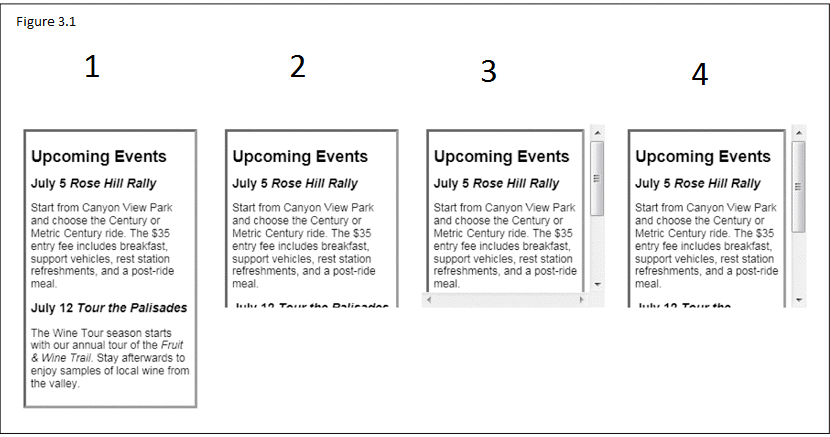
A. ?1 B. ?2 C. ?3 D. ?4
Computer Science & Information Technology