____ means a computer has been taken over by an unauthorized user.?
A. ?Pharmed
B. Phished
C. ?Hacked
D. ?Unsynced
Answer: C
Computer Science & Information Technology
You might also like to view...
For the network shown in Figure 9-15, what is the hop count from Router3 to subnet A?
Figure 9-15
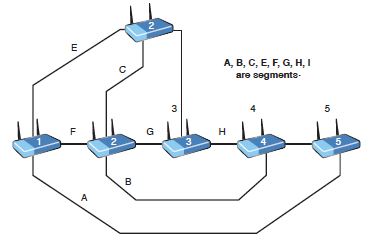
Computer Science & Information Technology
COGNITIVE ASSESSMENT For which purpose might you use a CSC?
A. To save content from a text to your phone. B. To text a friend a link to a website. C. To receive a notification from a website. D. To send a message to your mobile service provider.
Computer Science & Information Technology