The law requires search warrants to contain specific descriptions of what's to be seized. For cloud environments, the property to be seized usually describes physical hardware rather than data, unless the CSP is a suspect.
?
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
When you drag an action or message block to a new position, a(n) ________ displays where the box can be dropped
A) select icon B) orange line C) Access logo D) mouse arrow
Computer Science & Information Technology
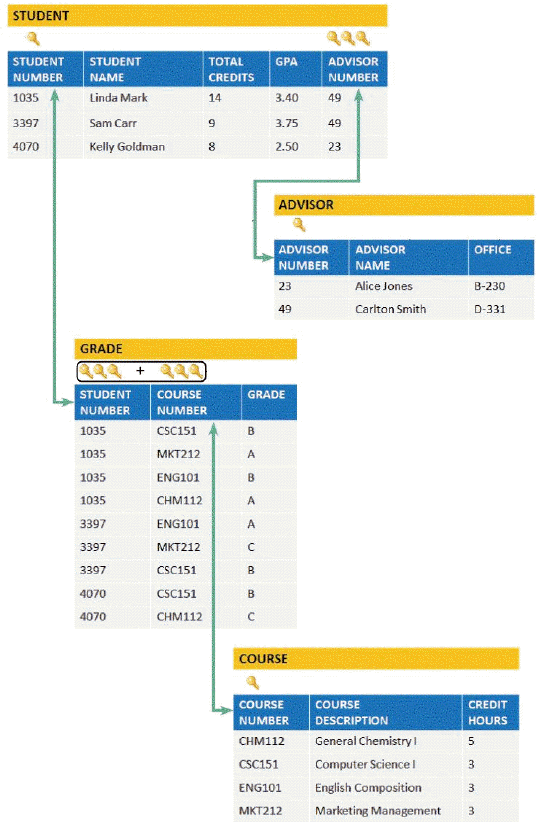
A. ?candidate key B. ?secondary key C. ?combination key D. ?foreign key
Computer Science & Information Technology