What two strategies are employed by the BSIMM security testing practice?
Fill in the blank(s) with the appropriate word(s).
Testing security functions with standard techniques and risk-based security testing
Computer Science & Information Technology
You might also like to view...
A ____ is a function that returns a true or false value instead of a numeric value.
A. Boolean function B. K-function C. Beta function D. Gamma function
Computer Science & Information Technology
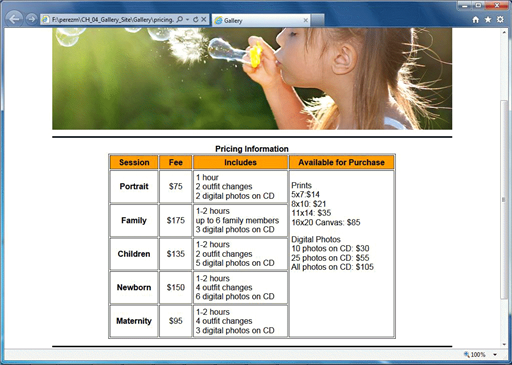
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology