Configure switch 1 (sw1), router R1, PC1, PC2, and S1 using the IP addresses provided in Table 1. The IP addresses used in this exercise will all be configured as part of a 192.168.5.0 network.
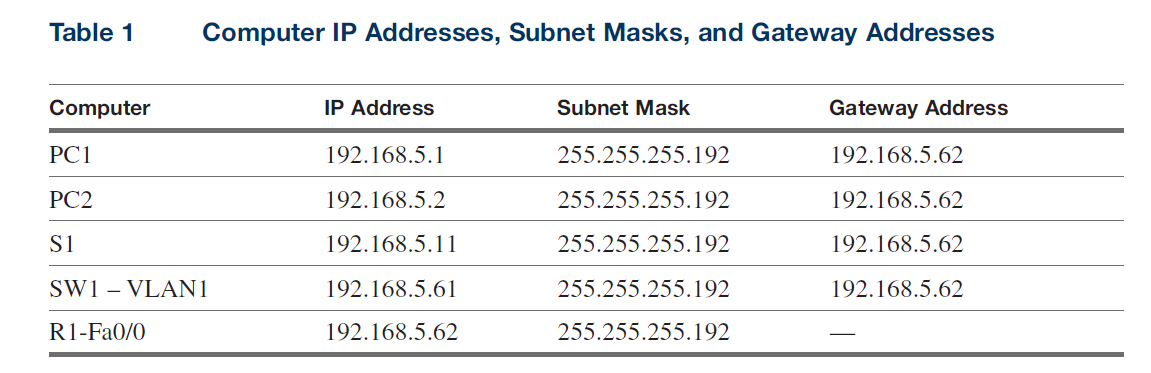
1. Your first task is to configure the switch SW1, the Router R1, the computers PC1 and PC2, and the switch S1 for the network provided in Figure 1. Use the IP addresses provided in Table 1.
2. After you have completed configuring the interfaces, verify that you have connectivity with all interfaces. List the commands used to verify network connectivity. Correct problems as needed.
3. Check whether port security has been enabled on the switch port connected to server S1 by using the show port-security interface Gi0/1 command. Record the status of the port security configuration on the interface based on the first line of output.
4. Configure port security using three commands: one command to make the port a statically configured access port, one command to enable port security, and one command to define the allowed MAC address, namely, S1’s MAC address of 0200.AAAA.AAAA. Record the three commands you used on the lines below.
5. Move back to enable mode and repeat the comman
1.
```
PC1
C:\> ip address 192.168.5.1 255.255.255.192
C:\> gateway 192.168.5.62
PC2
C:\> ip address 192.168.5.2 255.255.255.192
C:\> gateway 192.168.5.62
S1
C:\> Ip address 192.168.5.11 255.255.255.192
C:\> gateway 192.168.5.62
Switch 1
SW1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)# interface vlan 1
SW1(config-if)# ip address 192.168.5.61 255.255.255.192
SW1(config-if)# ip default-gateway 192.168.5.62
R1
R1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# int fa0/0
R1(config-if)# ip address 192.168.5.62 255.255.255.192
R1(config-if)# no shut
```
2. To verify network connectivity, you need to ping all interfaces. You can do this from any of the computers. In this case, the ping is coming from PC2.
```
C:\> ping 192.168.5.11
C:\> ping 192.168.5.1
C:\> ping 192.168.5.2
C:\> ping 192.168.5.61
C:\> ping 192.168.5.62
```
3.
```
SW1# sh port-security interface gigabitEthernet 0/1
Port Security : Disabled
Port Status : Secure-down
Violation Mode : shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 0
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0200.AAAA.AAAA
Security Violation Count : 0
```
4.
```
SW1(config-if)# switchport mode access
SW1(config-if)# switchport port-security
SW1(config-if)# switchport port-security mac-address 0200.AAAA.AAAA
```
5.
```
SW1# sh port-security interface gigabitEthernet 0/1
Port Security : Enabled
Port Status : Secure-Up
Violation Mode : shutdown
Maximum MAC Addresses : 1
```
Note that the violation mode and maximum number of MAC addresses are default settings
that can be configured.
6.
```
SW1# show mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- -----
ALL 0100.0ccc.cccc static CPU
ALL 0100.0ccc.cccd static CPU
ALL 0180.c200.0000 static CPU
ALL 0180.c200.0001 static CPU
ALL 0180.c200.0002 static CPU
ALL 0180.c200.0003 static CPU
ALL 0180.c200.0004 static CPU
ALL 0180.c200.0005 static CPU
ALL 0180.c200.0006 static CPU
ALL 0180.c200.0007 static CPU
ALL 0180.c200.0008 static CPU
ALL 0180.c200.0009 static CPU
ALL 0180.c200.000a static CPU
ALL 0180.c200.000b static CPU
ALL 0180.c200.000c static CPU
ALL 0180.c200.000d static CPU
ALL 0180.c200.000e static CPU
ALL 0180.c200.000f static CPU
ALL 0180.c200.0010 static CPU
ALL ffff.ffff.ffff static CPU
1 0200.1111.1111 dynamic Fa0/1
1 0200.2222.2222 dynamic Fa0/2
1 0200.AAAA.AAAA static Gi0/1
1 0200.BBBB.BBBB dynamic Fa0/3
```
Note: All MAC addresses configured by port security are statically stored in the MAC
address table.
7.
```
For PC1
C:\> ipconfig /all
IP Configuration
Physical Address. . . . . . . . . : 0200.1111.1111
For PC2
C:\> ipconfig /all
IP Configuration
Physical Address. . . . . . . . . : 0200.2222.2222
```
8.
```
For PC1
SW1(config)# int fa0/1
SW1(config-if)# switchport mode access
SW1(config-if)# switchport port-security
SW1(config-if)# switchport port-security mac-address 0200.1111.1111
For PC2
SW1(config-if)# int fa0/2
SW1(config-if)# switchport mode access
SW1(config-if)# switchport port-security
SW1(config-if)# switchport port-security mac-address 0200.2222.2222
SW1(config-if)#
```
9.
```
SW1# sh port-security interface fa0/1
Port Security : Enabled
Port Status : Secure-Up
```
10.
```
SW1# sh port-security interface fa0/2
Port Security : Enabled
Port Status : Secure-Up
```
11.
```
SW1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)# interface gigabitEthernet 0/1
SW1(config-if)# switchport mode access
SW1(config-if)# switchport port-security
SW1(config-if)# switchport port-security mac-address 0200.1111.1111
SW1(config-if)# switchport port-security violation protect
C:\> ping 192.168.5.11
Pinging 192.168.5.11 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 192.168.5.11
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
```
The connection to the switch has been disabled. The port has been secured and the MAC
address doesn’t match S1.
12.
```
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# int fa0/3
Switch(config-if)# switchport mode access
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security maximum 6
```
13.
```
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# int fa 0/6
Switch(config-if)# switchport mode access
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security violation shutdown
Switch(config-if)#
```
14.
Shutdown: Sets the violation mode and action to be taken when a security violation is
detected.
Restrict: This option will alert the network administrator and will allow traffic from the
allowed MAC address.
Protect: This option only allows traffic from the secure port and drops packets from
other MAC addresses.
You might also like to view...
The TODAY and NOW functions are in the ________ category in the Function Library group of the Formulas tab
A) Lookup & Reference B) Math & Trig C) Date & Time D) More Functions
When the Markers option in the Design contextual tab is checked, ________
A) marks for the first and last data values are placed on the sparklines B) a mark for only the low data value is placed on the sparklines C) a mark for each data value is placed on the sparklines D) a mark for only the high data value is placed on the sparklines