What List action does this depict?
Given the following diagram.
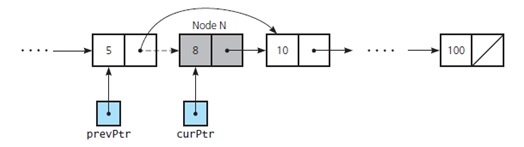
a. insert a new node
b. get the value stored at a node
c. remove a node from the chain
d. get the value stored at a node
c. remove a node from the chain
You might also like to view...
The future value of an asset can be calculated when ________ are constant over time
A) investments B) payments C) withdrawals D) deposits
A bank wants to store the account number of its customers (an 8-digit number) in encrypted form on magnetic stripe ATM cards. Discuss the security of the following methods for storing the account number against an attacker who can read the magnetic stripe: (1) store a cryptographic hash of the account number; (2) store the ciphertext of the account number encrypted with the bank's public key
using a public-key cryptosystem; (3) store the ciphertext of the account number encrypted with the bank's secret key using a symmetric cryptosystem. What will be an ideal response?