FIGURE 9-2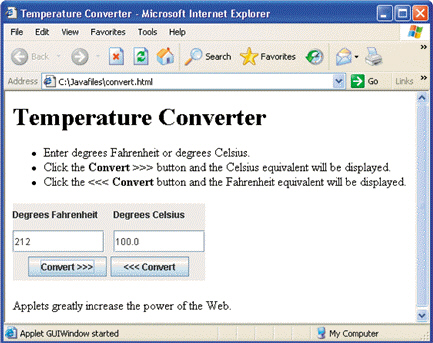 Figure 9-2 above shows an example of a(n) ____.
Figure 9-2 above shows an example of a(n) ____.
A. applet
B. table
C. inline image
D. associative link
Answer: A
Computer Science & Information Technology
You might also like to view...
Define color triad and discuss how it is used in design to devise a color scheme.
What will be an ideal response?
Computer Science & Information Technology
PSK keys are automatically authenticated between devices after a specified period known as the ____.
A. MIC interval B. IV interval C. rekey interval D. CRC interval
Computer Science & Information Technology